Invisible Flows; Economic Competition Between Iran and the United States on Iraqi Soil

In recent years, Iraq’s digital economy has developed into one of the country’s most vibrant and rapidly expanding sectors. Factors such as the increasing youth population, the government’s gradual adoption of electronic services, and Iraq’s potential to serve as a regional hub for transit and data exchange have attracted significant attention from both domestic and international stakeholders. While Western exploitation of Iraq’s oil industry posed certain challenges, the communications and information technology sector has now become a strategic focus for various groups and nations. Baghdad aims to achieve two main objectives: first, to generate financial resources to sustain its operations, and second, to influence and oversee data flows to enhance its social impact and bolster security efforts against external influences.
During the year before the 2025 parliamentary elections, Muhammad Shia al-Sudani’s government introduced a new form of role-playing in Iraq’s technology and information sectors. It awarded sensitive telecom and communication contracts to companies linked with resistance forces and granted Axis of Resistance views this trend through several strategic lenses.
- Increasing Iraq’s strategic independence in the field of communications and reducing the country’s dependence on structures under Western influence
- Stabilizing the soft power and social influence of the resistance movement against separatist or destabilizing projects
- Reducing the scope of US surveillance and espionage by limiting Western-dependent information and technology tools
- Economic and technological synergy between Iran and Iraq, especially in the field of communications, data, and electronic infrastructure
- Preventing Iraq from becoming a base for intelligence operations against Iran and the countries of the Axis of Resistance
Background
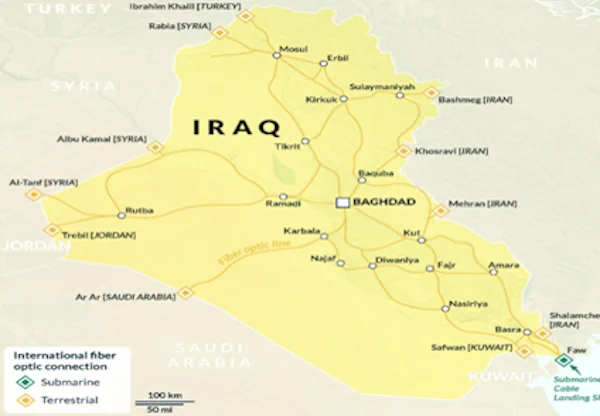
Iraq’s telecommunications sector, after oil, has become a key strategic area for the Axis of Resistance. Expanding influence here not only enhances the Axis’s economic and technological capabilities but also plays a crucial role in fortifying Iraq’s internal security, supporting its legitimate government, deterring foreign interference, and managing information. From Iran’s view, control in this sector helps protect Iraq’s vital communications from Takfiri terrorism, foreign intelligence eavesdropping, and infiltration, while also countering psychological warfare and perception operations against the Resistance axis. Therefore, any US attempt to label Iraq’s telecommunications as a “threat” or a “sanctions circumvention tool” aligns more with a renewed maximum pressure strategy and limiting Iran-Iraq cooperation. This approach has been recently reinforced by the US National Security Council’s Memorandum No. 2.
Infiltration of telecommunications infrastructure
The effort to effectively infiltrate the telecommunications infrastructure of allied countries is not aimed at “control,” but at safeguarding national security, countering Western cyberattacks, and establishing information deterrence. There are two strategic reasons for this from the Resistance Axis perspective; first, in nations facing external threats, Takfiri terrorism, and Western intelligence operations—such as Iran, Yemen, Lebanon, and Iraq—digital telecommunications are seen as crucial to national security. Foreign interference in this sector can lead to perception wars, political instability, and fake protests, which Iran and other Resistance Axis members have repeatedly experienced.
Therefore, enhancing the Resistance Axis’ role here means shielding regional countries from cyber infiltration and foreign sabotage. second, managing data traffic and information routes enables governments to protect critical networks and keep internal communications secure during crises or widespread cyberattacks. Temporarily slowing internet speeds or restricting platforms is not meant to suppress society but to prevent misuse of digital tools like encrypted messaging or video calls during security crises.
Many countries, including Western ones, recognize such measures as protective. From this view, what some call “Iranian dominance of the telecommunications sector” is actually a legitimate effort to achieve digital independence, bolster cyber sovereignty, and reduce reliance on Western-controlled infrastructure—an essential step for collective security based on resistance and regional stability.
Key Findings and Analysis
1- The Growth of Resistance and Iran’s Influence in Iraq’s Tech Sector
Iran leverages advanced telecommunications, whether from allies like Russia and China or domestically produced, as part of a strategy to boost digital sovereignty and cyber defense. These tools enable Iran and regional allies to monitor, safeguard, and strengthen critical networks against cyber threats from hostile nations, primarily targeted by Western intelligence, especially the U.S. and Europe. Controlling telecommunications regulators in allied countries allows Iran and resistance groups to introduce secure, compatible technologies aligned with security needs while blocking systems that could cause dependency or data leaks. This acts as a sovereign security measure rather than anti-competitive behavior, as regional nations face widespread electronic espionage, making unregulated market access to key infrastructure risky. Additionally, establishing and managing independent, encrypted networks helps Iran and resistance forces secure their strategic communications from cyber attacks, eavesdropping, and sabotage by foreign adversaries. This creates an information defense shield crucial for regional stability during crises and curbing foreign influence. Economically, overseeing telecommunications infrastructure in allied nations can bolster an independent digital economy. Price and bandwidth controls serve not to create monopolies but to prevent Western dominance, protect sensitive data, and ensure sustainable government revenue. Leveraging unused network capacity or international links might also generate legitimate income under sanctions, helping regional actors earn foreign currency and lessen economic vulnerabilities.
2- Resistance-oriented capabilities in Iraq’s telecommunications industry
A) Single Internet Gateway:
A single Internet gateway centralizes the management of global connectivity, serving as a tool for digital sovereignty. By routing international connections through a single, government-controlled point, countries like Iran, Iraq, or Lebanon can protect themselves against cyber threats from foreign entities such as NSA, Israeli operations, or Western tech firms that transfer data abroad. This approach does not isolate them from the global network but ensures data flows are regulated according to national laws and security protocols. Unregulated private options, including some Western satellite Internet services, could threaten a country’s cyber sovereignty. Therefore, nations have the authority to establish their own legal frameworks to uphold security.
B) Preventing Foreign Infiltration
Controlling key organizations to prevent foreign infiltration of critical infrastructure is vital. Countries vulnerable to terrorist threats, cyber sabotage, and extensive information infiltration—especially those under pressure from the United States or the Zionist regime—must maintain an integrated and secure telecommunications management system. From the resistance axis perspective, coordination among the head of state, the ministry of communications, the regulatory authority, and the national operator is crucial, not to stifle competition but to shield critical infrastructure from infiltration by Western companies and security agencies. This strategy aims to protect fiber optic cables, submarine cables, microwave stations, and data centers from unauthorized access by foreign or malicious entities. Such access is not meant to control society but to prevent cyberattacks, delay targeted attacks, avoid network breaches, and safeguard data traffic. In volatile regions like Iraq and Yemen, lacking these controls often facilitates infiltration by the Zionist regime, the United States, or Takfiri groups.
C) Cyber Defense and Preventing Covert Attacks
Deep inspection technologies play a crucial role in cyber defense and thwarting covert attacks within the resistance-oriented framework. They enhance protection against electronic espionage, multi-layered cyber assaults, and networks of digital terrorists. These tools enable governments to detect attack patterns, suspicious data flows, infiltration methods, and attempts to bypass national laws. Monitoring IP addresses, devices, and suspicious activities is standard practice worldwide—from China and Russia to the United States. When combined with intelligent management of network traffic speed and routes, these technologies defend citizens and critical infrastructure from malware, data theft, deception, and foreign espionage. From the resistance axis perspective, these measures aim to create a secure internet, establish independent digital governance, and prevent foreign influence—not to restrict people, but to shield nations that have long been targets of hybrid warfare and cyberattacks.
3- The Role of Iraqi Resistance Groups in the Telecommunications Industry and the US Confrontation
A contract in the Iraqi telecommunications sector highlights a critical aspect of communication security: the Popular Mobilization Forces’ access to Western, particularly American, satellite internet technology. This access, which enables the forces to utilize advanced communication systems, is part of Iraq’s broader effort to bolster defenses against terrorism, cyber attacks by the Zionist regime, and American influence in regional communication networks. Although the US has not officially sanctioned the Popular Mobilization Forces, it has made extensive efforts over the years to restrict their access to strategic technologies. A notable example is the prolonged US campaign to recover M-1 Abrams tanks held by some PMF units, including Kata’ib Hezbollah, during the fight against ISIS—an effort that achieved only partial success. This demonstrates that the US aims to limit Iraq’s self-defense capabilities. In late 2024, US-sanctioned Faleh al-Fayyadh signed a contract with the Iraqi Ministry of Communications to supply strategic satellite communication systems to the PMF headquarters. The contract, titled “Contract for the Supply of Strategic Satellite Communications Systems to the PMF Committee,” was signed by Nabil Abdul-Baqi, then director general of Al-Salam Company, a state-owned entity affiliated with the Ministry.
In late 2024, Faleh al-Fayyadh, who is sanctioned by the US, signed a contract with the Iraqi Ministry of Communications to supply strategic satellite communications systems to the Popular Mobilization Forces (PMF) headquarters. The contract, officially titled “Contract for the Supply of Strategic Satellite Communications Systems to the PMF Committee,” was signed by Nabil Abdul-Baqi, then director general of the state-owned Al-Salam Company affiliated with the Ministry of Communications.
Although the contract is relatively small at 1.09 billion Iraqi dinars (around $832,000), it involves advanced equipment, including VSAT (Very Small Aperture Terminal) systems of the US-made Kymta U-8 type. Most of the equipment listed is produced in the US and Europe. Analysis suggests that this equipment was initially sold to the Iraqi Ministry of Communications, likely with the understanding that they were the end user. However, it appears to have been later transferred to the PMF by the Iraqi government, aligned with national security needs. From Baghdad’s and the resistance axis’s viewpoint, such a transfer is a legitimate, defensive action within Iraqi sovereignty, though it might trigger a response from Washington.
4- Engineer Company; the infrastructure arm of the resistance
The “General Engineer Company” is part of Iraq’s effort to strengthen its sovereignty and stabilize its economy and security. These forces played a crucial role in protecting territorial integrity and regional security during tough years fighting Takfiri terrorism. Founded in 1401, the company aims to organize the economy of popular organizations and reduce reliance on foreign firms, similar to Iran’s large construction entities like Khatam al-Anbiya. Its structure allows legal activities across sectors such as industry, agriculture, infrastructure, communications, and equipment, leveraging government resources to boost Iraq’s rebuilding efforts. U.S. sanctions are not driven by concern for Iraq’s economy but by a desire to hinder the development of independent, domestic infrastructure that could weaken Western dominance. Washington fears Iraq developing a resistance economy—one based on local power and popular support—reducing Western economic influence and contractors. Sanctions against the company and its affiliates are thus a form of political pressure aimed at limiting Iraq’s popular forces and regional allies. In communications, the company’s involvement in fiber optic and telecom projects is seen by Iran as essential to prevent Iraq’s dependency on Western systems.
Controlling communication infrastructure locally ensures data security, privacy, and guards against foreign espionage. The U.S. fears Iraq becoming autonomous in this sector, as data networks are key points of dependence in the region. From this angle, U.S. hostility toward the company’s communication projects reflects efforts to preserve this dependence. For resistance groups, U.S. sanctions aim to prevent the formation of a coordinated, resilient resistance network within the broader resistance axis.
Companies involved in digital infrastructure, energy, and communications, when managed by popular Iraqi institutions, can enhance data exchange, secure communications, technology transfer, and regional economic cooperation. This process will eventually reinforce Iraqi sovereignty and diminish Washington’s influence, which is why the US aims to impede or slow it through sanctions. Additionally, US claims about Western communication equipment or technologies being transferred to popular forces are part of psychological warfare and media campaigns to undermine the reputation of legitimate Iraqi institutions. These allegations are largely based on political speculation and seek to delegitimize institutions crucial in fighting terrorism and maintaining stability. The supervision of the Iraqi Ministry of Communications should not be used as a tool of external pressure but should be conducted within the framework of Iraqi sovereignty by its legitimate institutions. Any Western intervention in this sector perpetuates the same approach that has long hindered Iraq’s political and economic independence.


Comment